Admin Access
Introduction
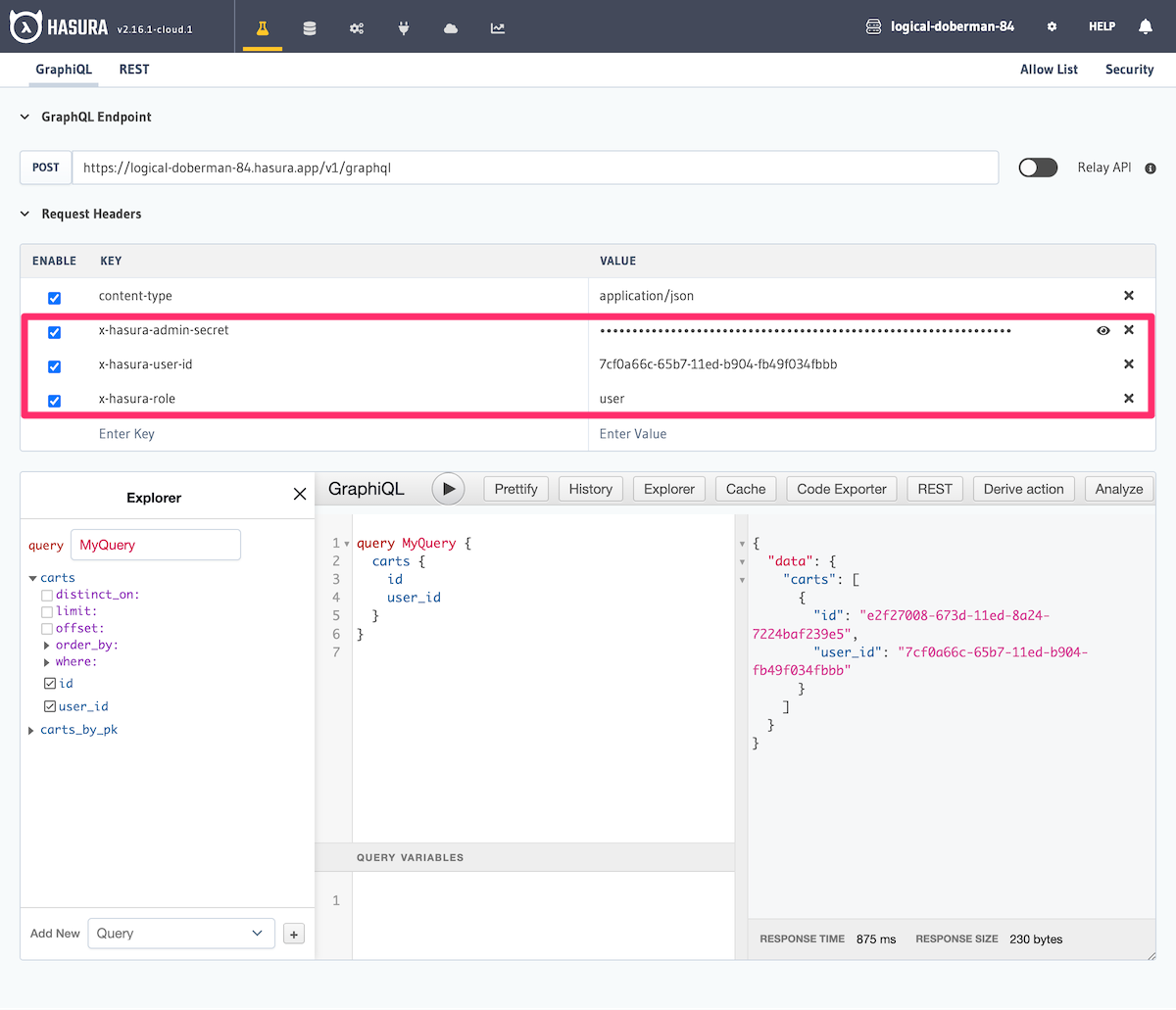
Hasura will bypass permissions and allow all queries, mutations and subscriptions when you include your
X-Hasura-Admin-Secret header without other session variables on your request. You can also specify the admin
role in your authenticated requests to bypass permissions.
The admin secret should never be exposed in front-end clients where it could be accessed by a malicious user by inspecting the request.
Admin secret in combination with other session variables
If you include the X-Hasura-Admin-Secret header and also add the X-Hasura-Role and other user specific
headers such as X-Hasura-User-Id, Hasura GraphQL Engine will process the request using the defined access-control
rules for that user and role and not as an admin.
Without the X-Hasura-Admin-Secret header you will need to authenticate your requests as a user and role with
either the JWT or webhook authentication methods.
Using the admin role
As an alternative to the admin secret header you can also make requests with the default admin user role. This
role allows you the user to perform any operation on any table and can be used where full unrestricted permissions
are required.
To use this role, your JWT or webhook token should provide the role as admin. You would still verify your request in
the normal way with Hasura Engine in either JWT or webhook authentication modes.