Configuring Permission Rules
Introduction
Permissions in Hasura are defined with table, role and operation (insert, update, select, delete) level granularity:
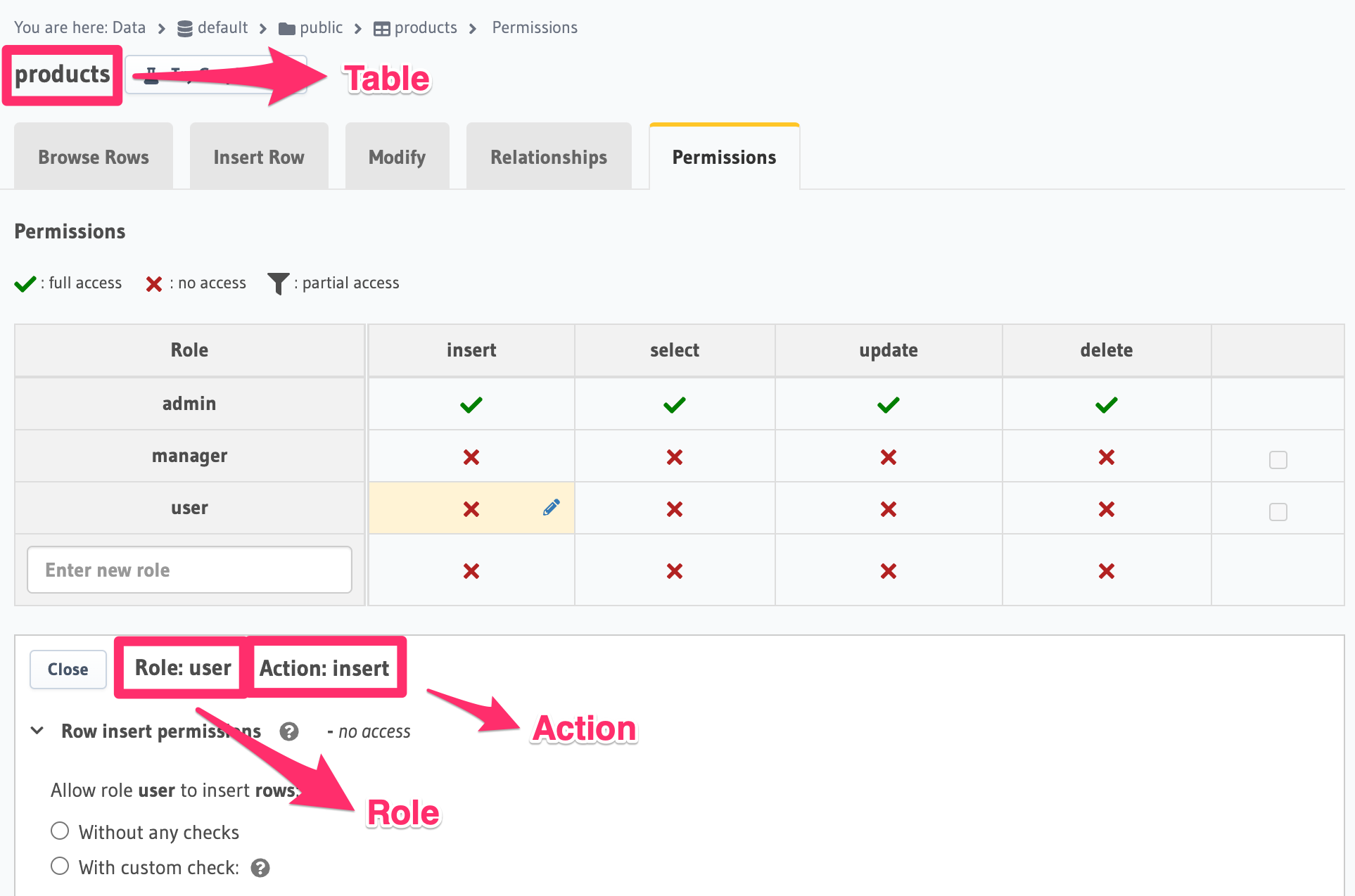
Requests to the Hasura GraphQL Engine should contain the reserved session variable
X-Hasura-Role (or X-Hasura-Allowed-Roles and X-Hasura-Default-Role) to indicate the requesting user's role.
The table and operation information is inferred from the request itself. This information is then used to determine
the right permission rule to be applied (if one has been defined) to the incoming request.
Hasura converts incoming GraphQL requests into a single SQL query which includes constraints derived from the permission rules that is executed on the configured database instance.
Permissions are essentially a combination of boolean expressions and column selections that impose constraints on the data being returned or modified.
Let's take a look at the different configuration options available to define a permission rule. Permission rules can be defined in the Console or the metadata APIs for permissions.
Operation permissions
Select permissions
For select operations or for GraphQL queries, you can configure the following:
Insert permissions
For insert operations or for GraphQL mutations of the type insert, you can configure the following:
Update permissions
For update operations or for GraphQL mutations of the type update, you can configure the following:
- Row permissions including Pre and Post update checks
- Column permissions
- Column presets
- Backend-only mutations
Delete permissions
For delete operations or for GraphQL mutations of the type delete, you can configure the following: