Authentication and Authorization
Introduction
Authentication verifies the identity of a user, while authorization determines what they can access.
Hasura provides flexible authentication and role-based access control (RBAC) authorization models.
Actual authentication is handled outside Hasura. Once a user is authenticated with your auth service, you can either i) provide a JWT to the Hasura GraphQL Engine containing session variables like user role and any other values like user id, or ii) specify a webhook in order to resolve the variables and send them back.
For authorization, Hasura helps you define granular, role and session variable based permission rules to control access to your data. These permissions utilize the session variables returned by your authentication service and are granular enough to control access to every row or column in your database.
Let's take a look at a high-level overview of how this works when Hasura GraphQL Engine receives a request:
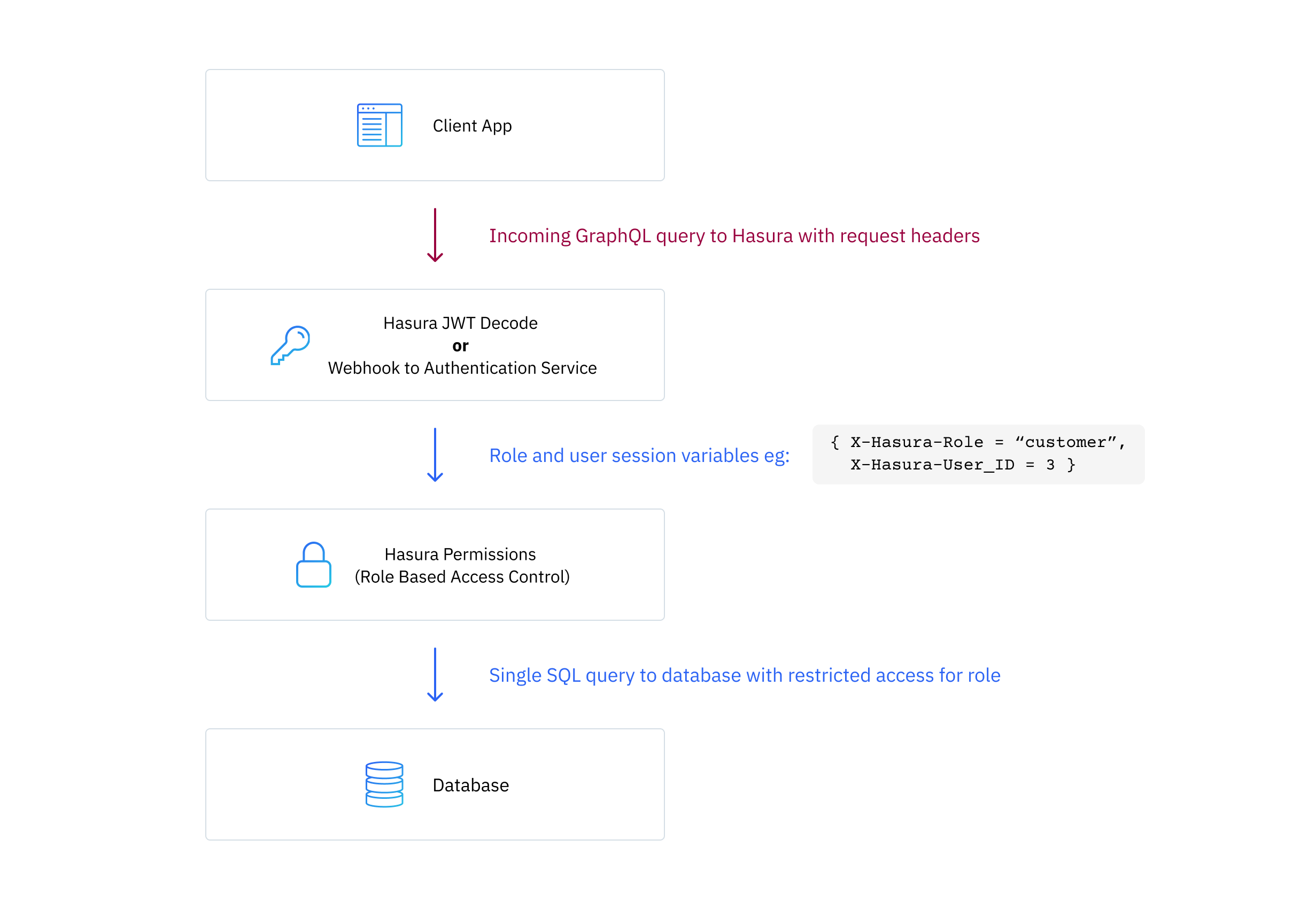
Hasura uses the role, session variables and the actual GraphQL query itself to validate against the authorization permission rules defined by you. If the operation is allowed, it generates an optimized SQL query, which includes the constraints from the permission rules, and sends it to the database to perform the required operation; fetching the required rows for queries or inserting, editing or deleting rows for mutations.
Hasura also provides functionality to enable authorization for its Actions and Remote Schema features too.
More details about setting up authentication and authorization permissions:
If you'd like to learn about authentication and authorization by following a tutorial, check out our Learn Tutorial, Authentication with Hasura.