Connecting Hasura to a Google Cloud SQL Postgres Database
Introduction
This guide explains how to connect a new or existing Google Cloud SQL Postgres database to a Hasura instance, either on Hasura Cloud or via one of our self-hosted solutions. If you're exploring Google Cloud SQL Postgres and are interested in migrating an existing Postgres database - such as from Heroku - check out their docs before continuing below.
If you plan on using Hasura Cloud, which we recommend, follow steps 1 and 2 below. If you're self-hosting a Hasura instance and already have a project running, skip to step 3.
Step 1: Sign up or log in to Hasura Cloud
Navigate to Hasura Cloud and sign up or log in.
Step 2: Create a Hasura Cloud project
On the Hasura Cloud dashboard, create a new project:
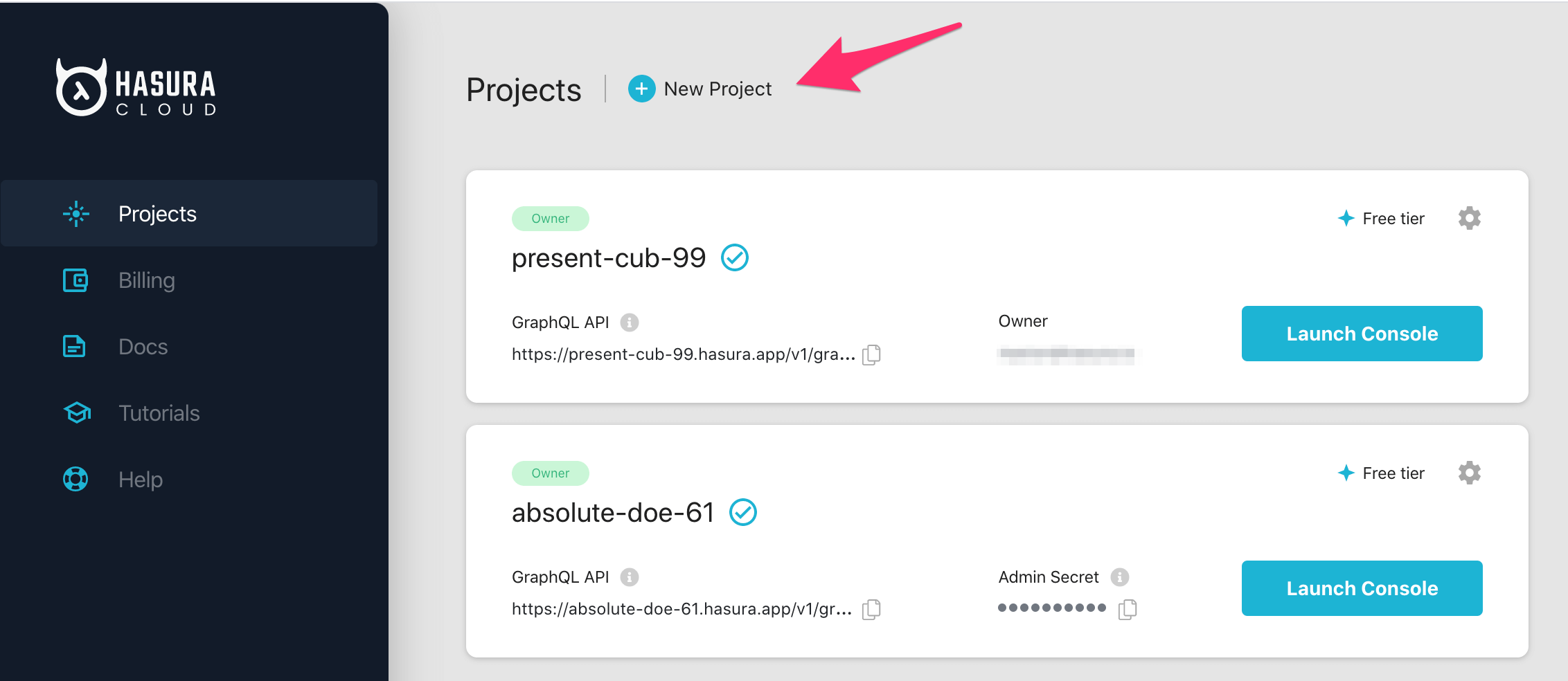
After the project is initialized successfully, click on Launch Console to open the Hasura Console in your browser.
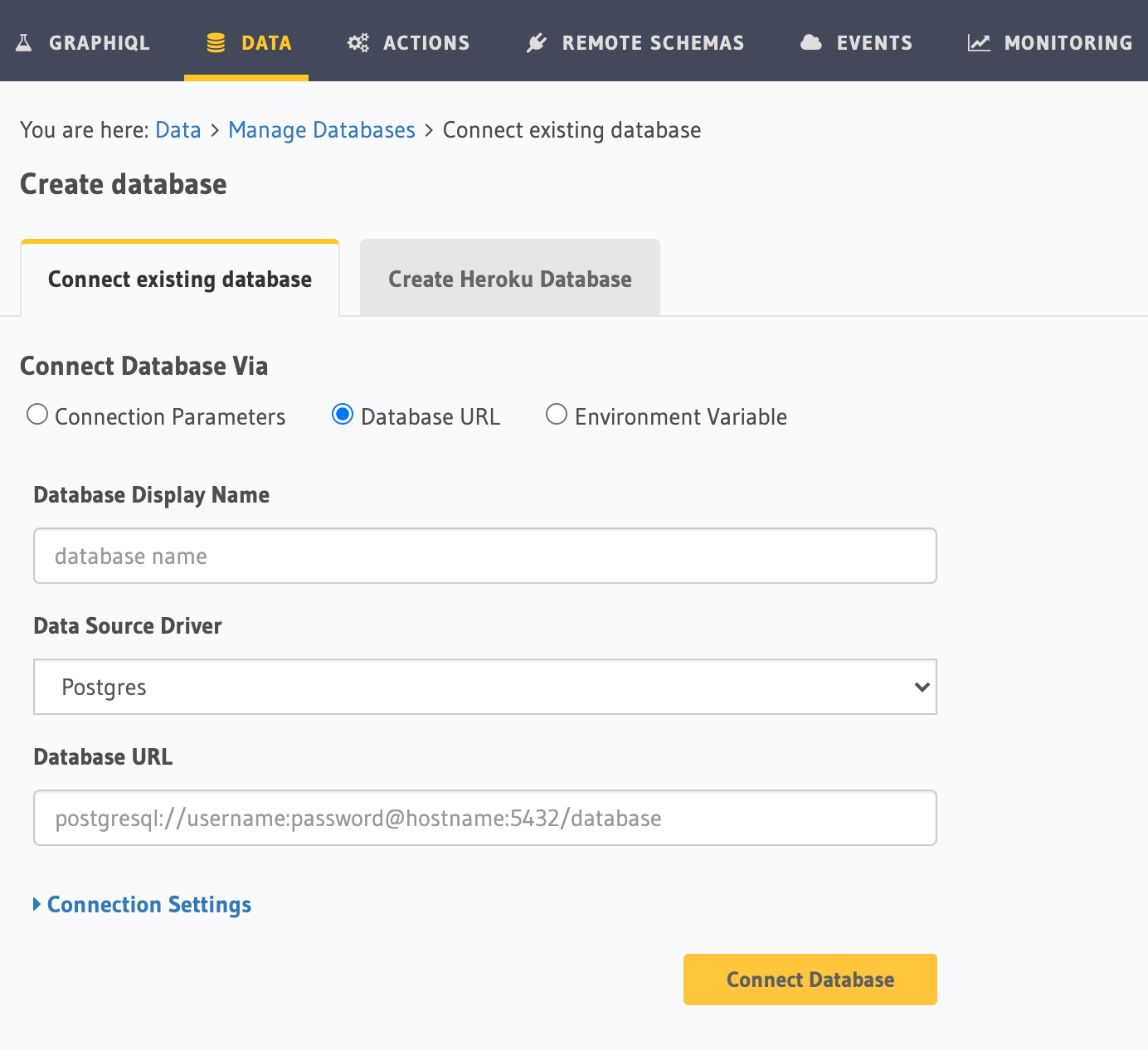
On the Hasura Console, navigate to the Data tab and choose Connect Existing Database. Hasura will prompt you for a
Postgres Database URL. We'll create this in the next step and then come back here.
Step 3: Create a Postgres DB on GCP
If you have an existing Postgres database on GCP, you can skip this step and move on to step 4.
Log into the GCP console.
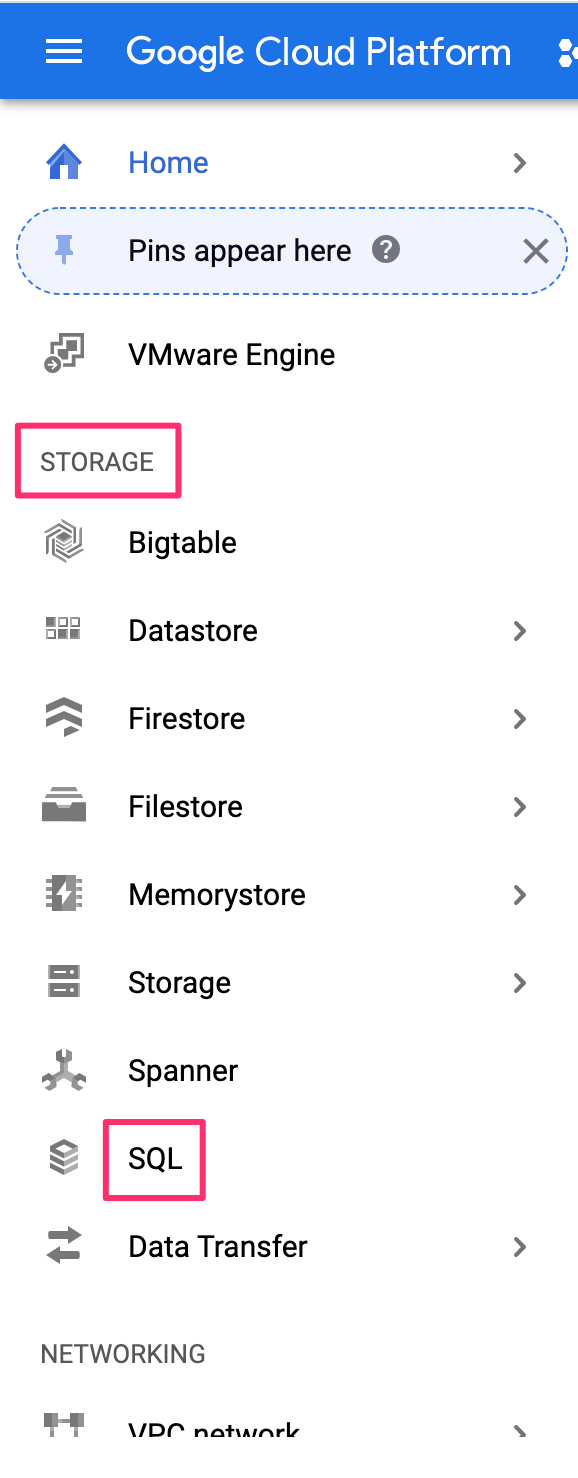
On the left-side navigation, scroll down to Storage and click on SQL:
On the top, click on Create instance:
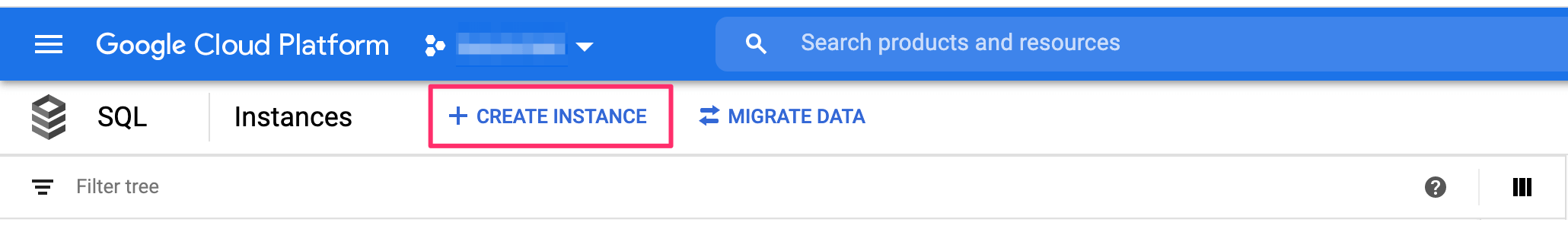
Select Postgres:
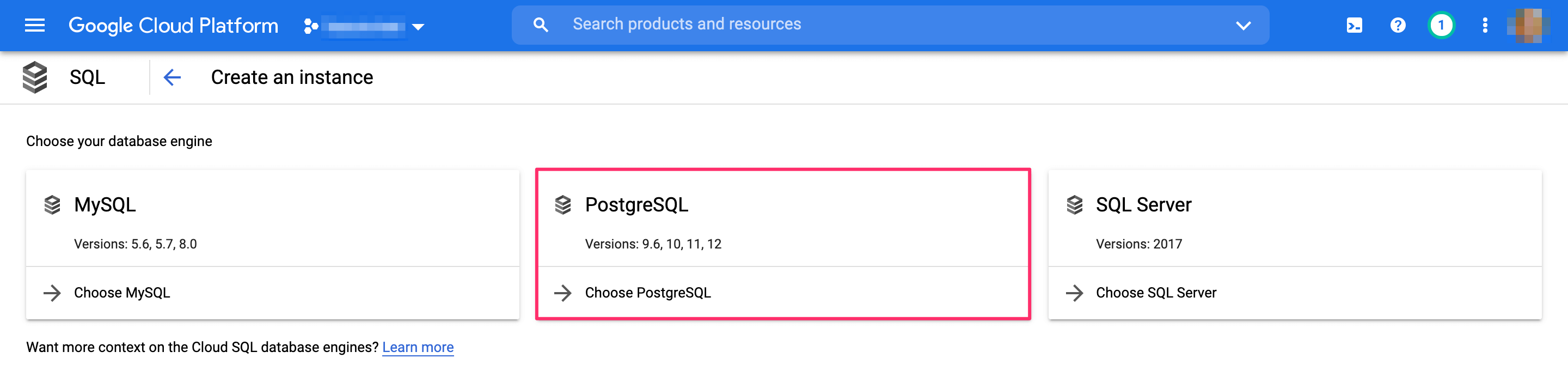
Select an instance ID, as well as a default user password. If required, choose a specific region and zone.
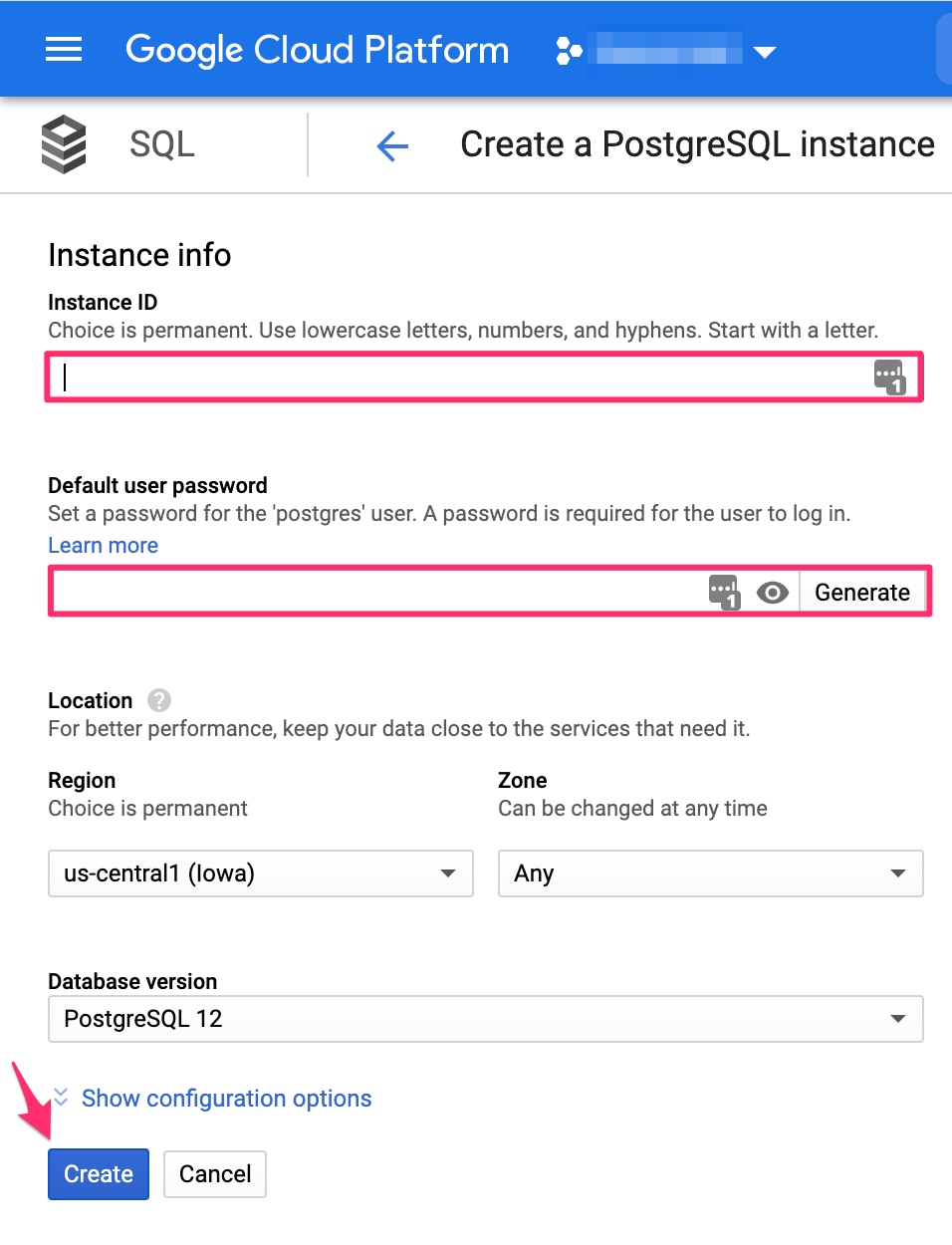
Then click Create.
Step 4: Allow connections to your DB from Hasura
On the dashboard of your GCP database instance, on the left sidebar, click on Connections. Then scroll down to the
checkbox Public IP, and click + Add network:
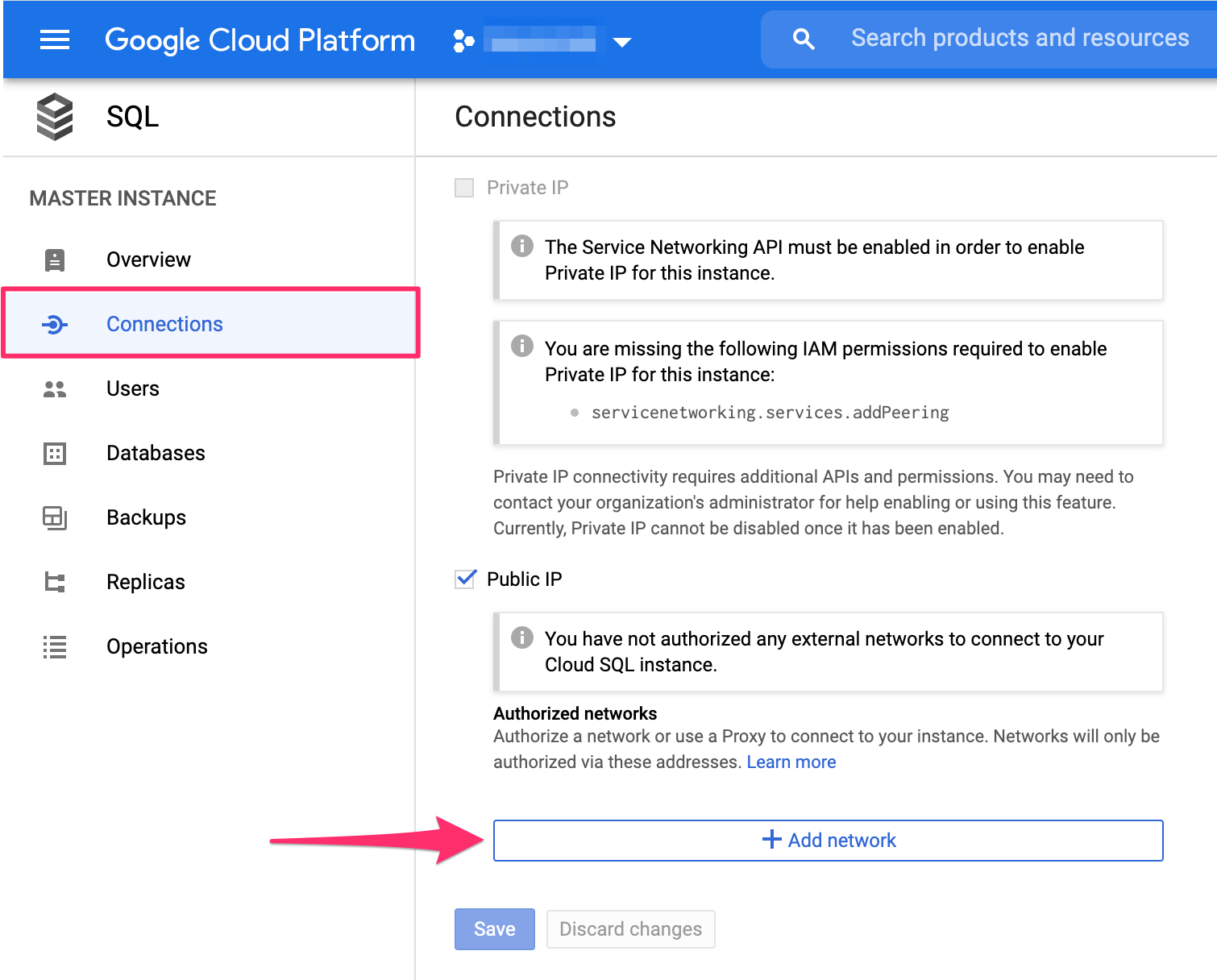
You can choose an optional name (e.g. "Hasura").
If using Hasura Cloud, from your project's dashboard, copy the Hasura Cloud IP address:
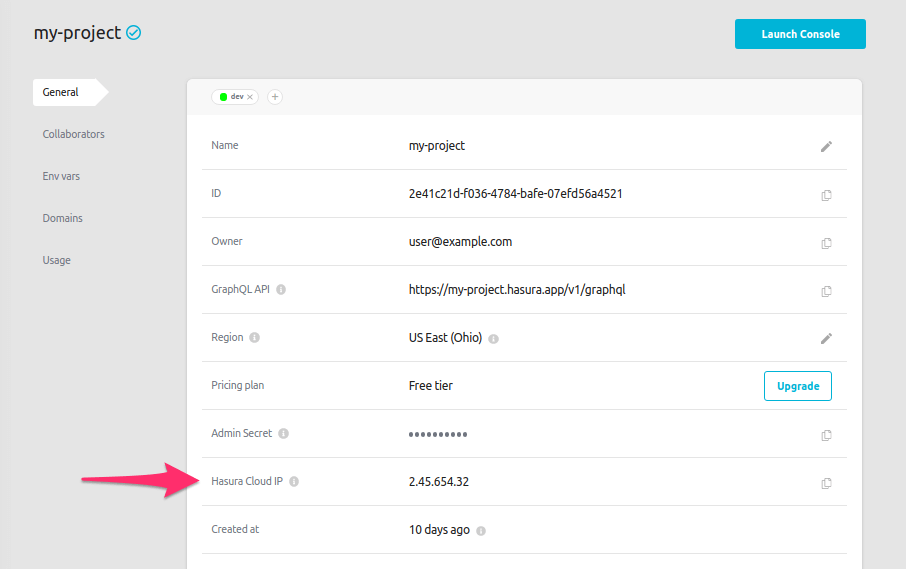
If you're using a self-hosted solution, you'll need to determine the IP address manually depending on your hosting service.
Enter the Hasura IP address that you copied:
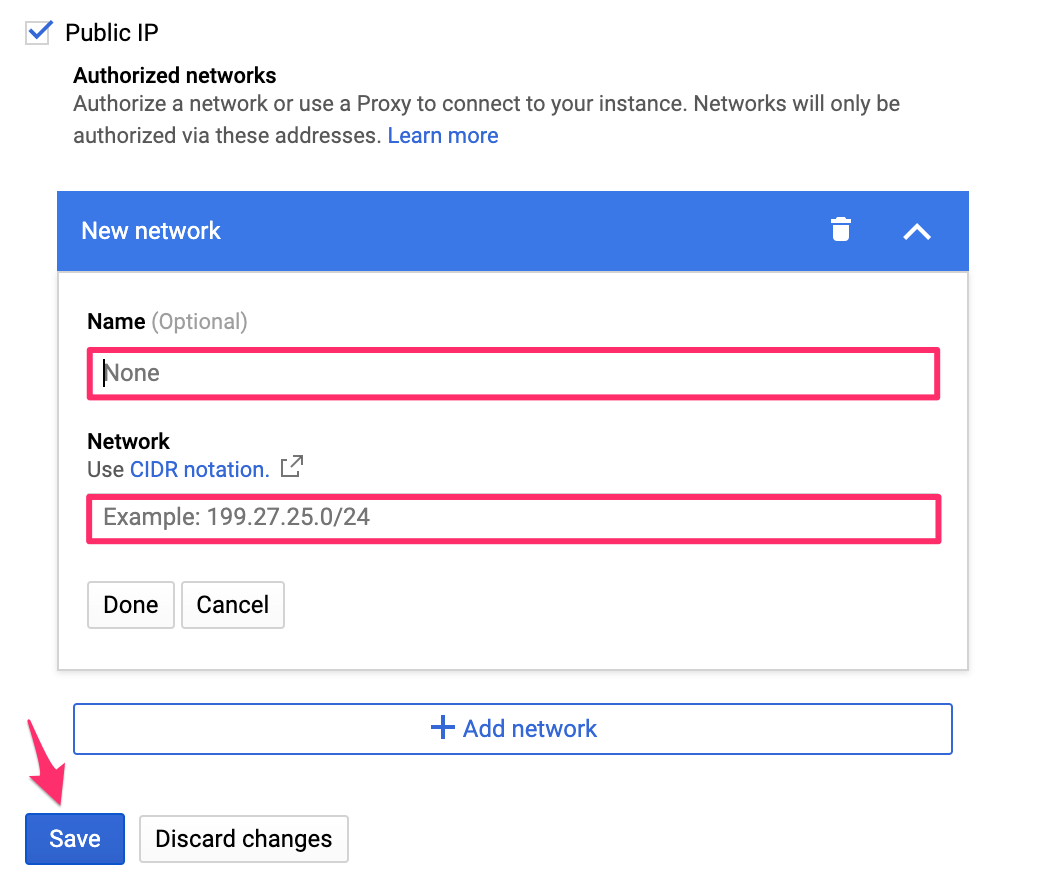
Then click Save.
If you're using a database user other than the default one, make sure to give it the right Postgres permissions.
Step 5: Construct the database connection URL
The structure of the database connection URL looks as follows:
postgresql://<user-name>:<password>@<public-ip>:<postgres-port>/
user-name: If you have a separate database user, the user name will be their name. If you didn't specify a user, the default user name ispostgres.password: If you have a separate database user, use their password. Otherwise, use the password that you chose when creating the database.public-ip: The public IP can be obtained by clicking onOverviewon the left-side navigation and then scrolling down toConnect to this instance:
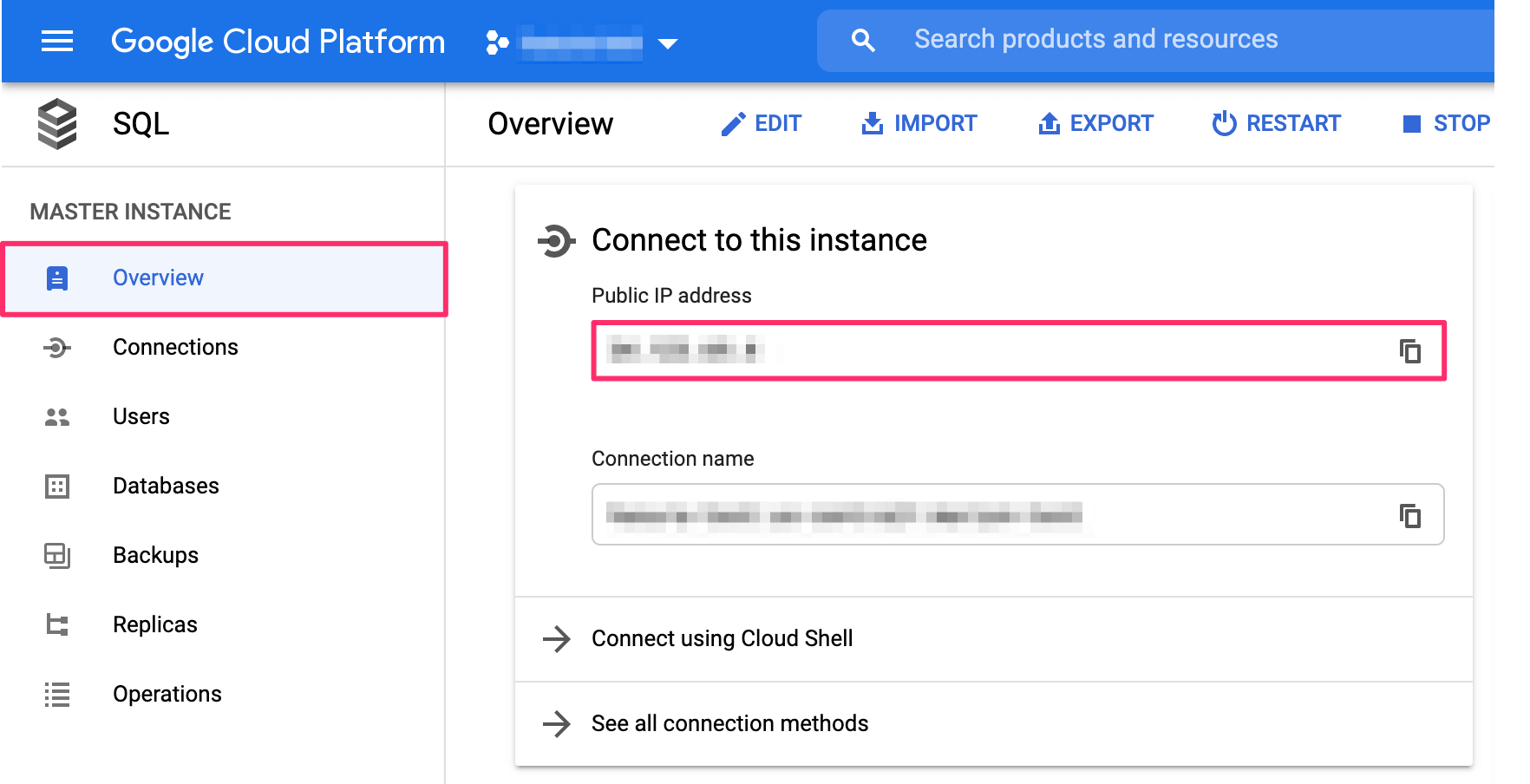
postgres-port: The default port for Postgres is5432if not specified otherwise.db: The DB ispostgresby default unless otherwise specified.
Step 6: Finish connecting the database
Back on the Hasura Console, enter the database URL that we retrieved in step 5:
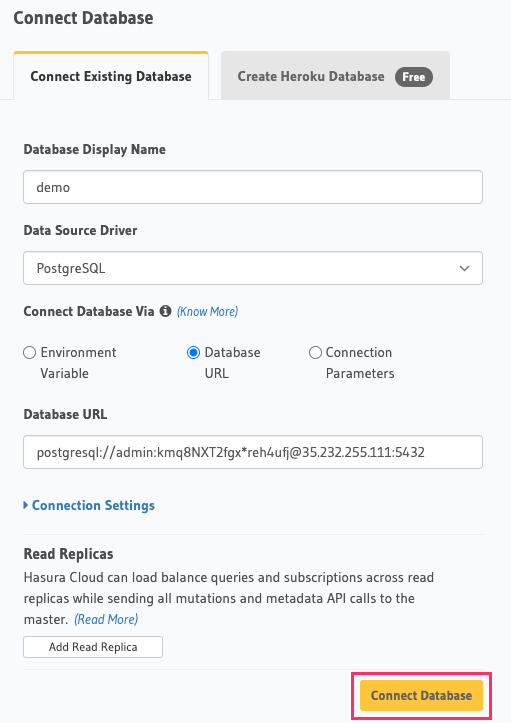
Then click Connect Database.
For security reasons, it is recommended to set database URLs as env vars and using the env vars to connect to the databases in place of the raw database URLs.
Voilà. You are ready to start developing.
Step 7 (optional): Enable SSL connection
Step 7.1 Get GCP SSL Certs
Google Cloud (GCP) SQL makes the following SSL/TLS certificates available for download:
- A server certificate saved as
server-ca.pem - A client public key certificate saved as
client-cert.pem - A client private key saved as
client-key.pem
Google Cloud Documentation for detailed information about the different certs.
Download these certs to your local drive.
Step 7.2: Add env vars
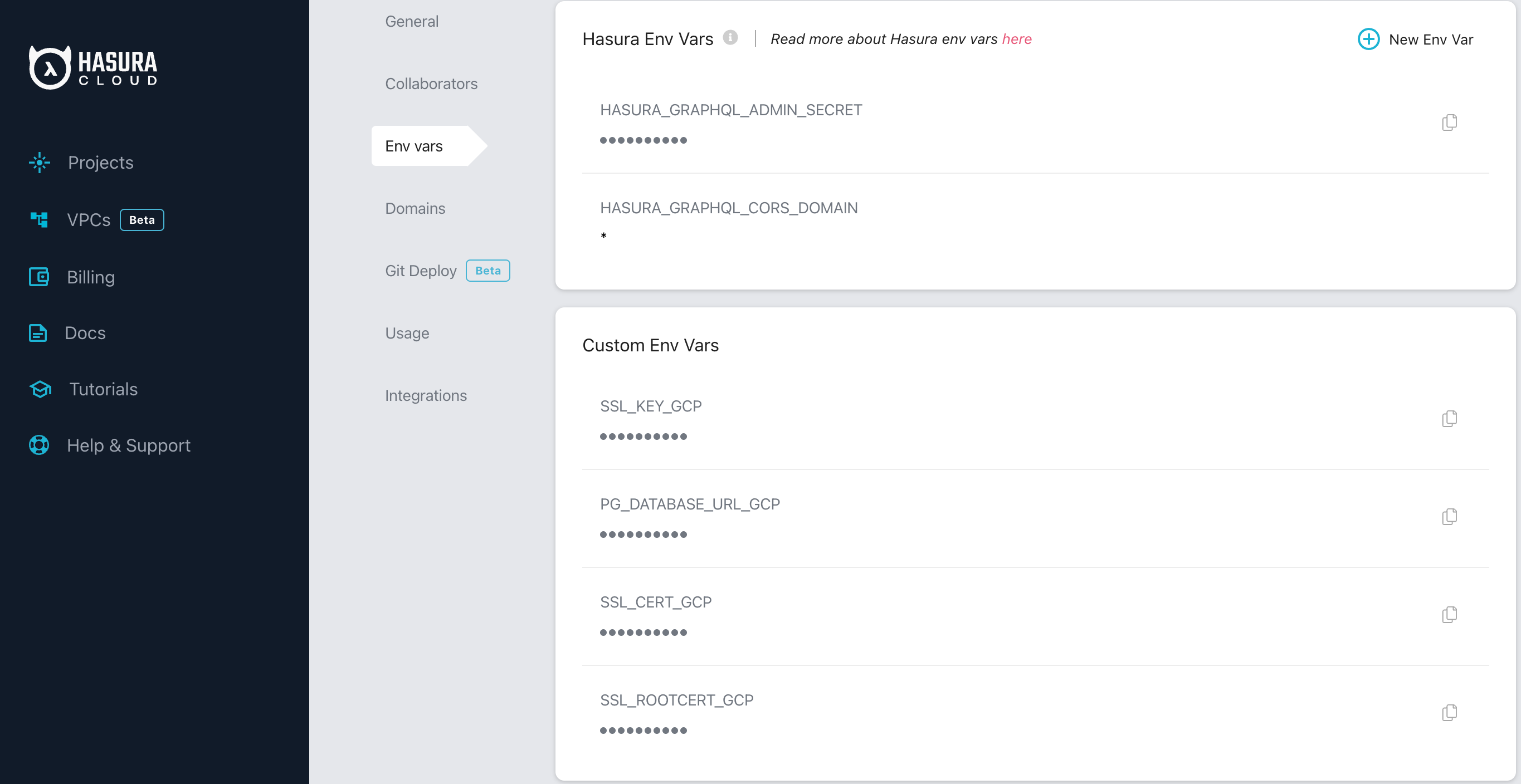
If using Hasura Cloud, go to your project and add the following env vars:
(Open the cert files using your favorite text editor, select all the contents and copy them to the clipboard)
| Env Var Name | Value |
|---|---|
SSL_ROOTCERT_GCP | Contents from server-ca.pem |
SSL_CERT_GCP | Contents from client-cert.pem |
SSL_KEY_GCP | Contents from client-key.pem |
Here is how your Hasura Cloud env vars setup should look like:
If you're using a self-hosted solution, you can set these env vars in your docker-compose.yml file.
Step 7.3: Configure SSL settings
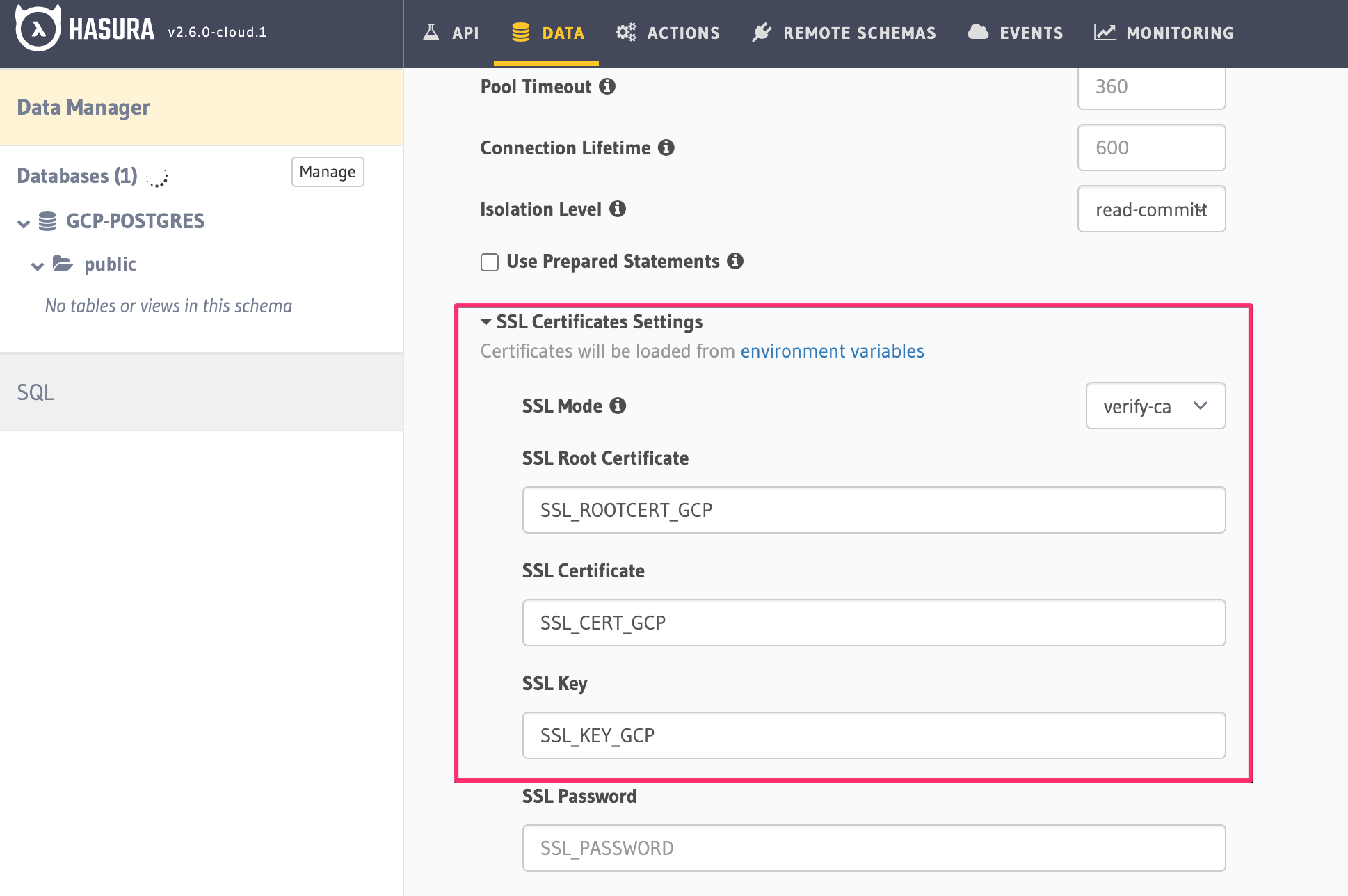
Open the Console of your Hasura Project, go to the Data -> Manage -> [db-name] -> Edit page.
Under Connection Settings add the following SSL certificate settings:
| Field Name | Value |
|---|---|
SSL Mode | verify-ca (select from dropdown) |
SSL Root Certificate | SSL_ROOTCERT_GCP |
SSL Certificate | SSL_CERT_GCP |
SSL Key | SSL_KEY_GCP |
Here is how the setup should look like:
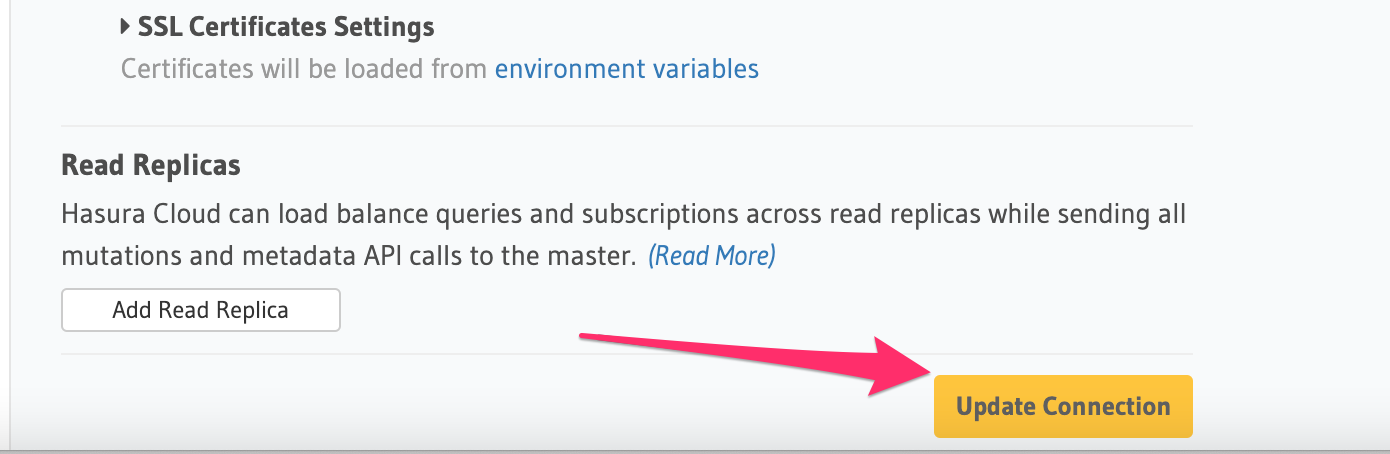
Finally, click on the Update Connection button to apply the SSL settings.
Next steps
You can check out our 30-Minute Hasura Basics Course and other GraphQL & Hasura Courses for a more detailed introduction to Hasura.
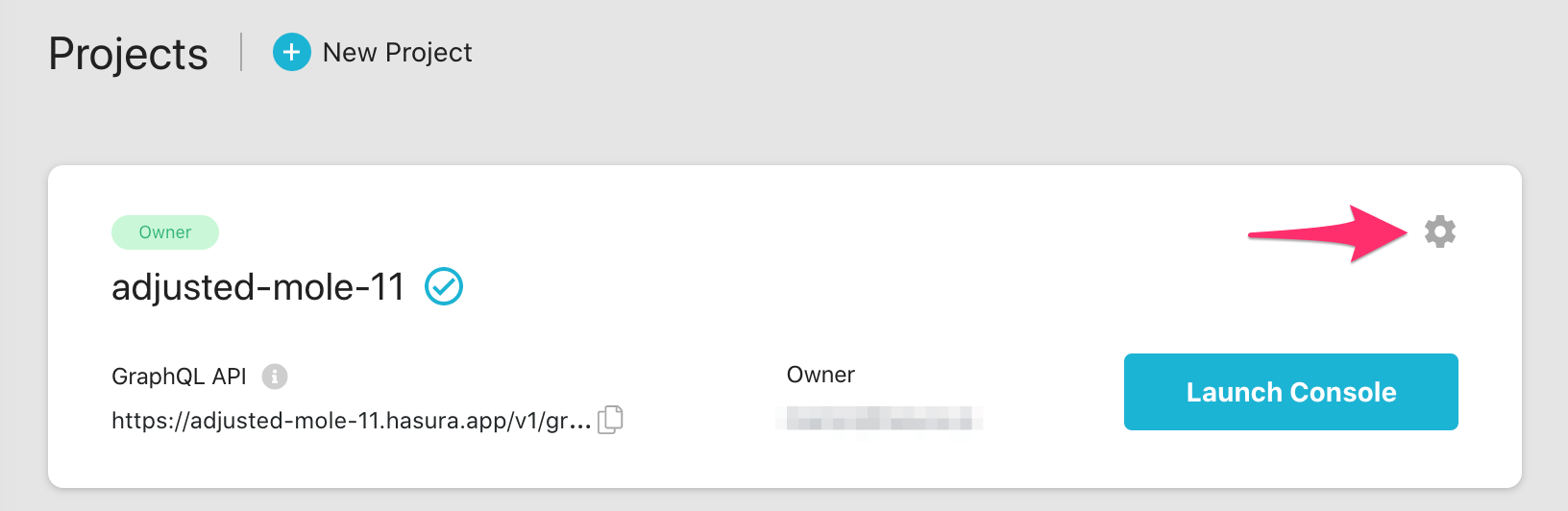
If using Hasura Cloud, you can also click the gear icon to manage your Hasura Cloud project. (e.g. add collaborators, env vars or custom domains).
For more information on which Postgres features we support, check out this page.