AWS Private Endpoints
Overview
AWS Private Endpoints leverage AWS PrivateLink technology to establish secure, private connectivity between your VPC and Hasura's Data Plane. This private connection ensures that your data traffic never traverses the public internet, significantly enhancing security and reducing exposure to potential threats.
How It Works
AWS PrivateLink uses AWS's internal network to create private connections between services. The process works as follows:
- You create a VPC Endpoint Service in your AWS account, backed by a Network Load Balancer. See Prerequisites section below
- You provide Hasura with your VPC Endpoint Service name
- Hasura creates a VPC Endpoint in the Data Plane VPC that connects to your endpoint service
- AWS creates Elastic Network Interfaces (ENIs) in the Data Plane subnets
- The Data Plane connects to your services through these ENIs
- All traffic remains on the AWS private network
Prerequisites
Before creating an AWS Private Endpoint, ensure you have the following:
-
A Private DDN Data Plane deployed in AWS
- Your Data Plane must be deployed and in an active state
- The Data Plane region should match the region where you want to create the private endpoint
-
An AWS VPC Endpoint Service in your AWS account
- In the same region as your Data Plane
- The "Acceptance Required" setting can be enabled or disabled based on your security requirements
- Created and configured with a Network Load Balancer (NLB)
-
If an RDS is used, Hasura recommends using AWS Lambda as a helper function to automate the registration of Amazon RDS instance IP addresses with a Network Load Balancer (NLB) target group. Please follow this external document for the setup required to do this. Below are a few important details:
- You, as the customer, are referenced as VPC-B within this doc.
- Skip any instructions in the document which reference VPC-A.
- For details on obtaining the Role ARN, refer to Step 1 under the Creating a Private Endpoint section below in this document.
Note that the purpose of the AWS Lambda in this solution is to:
- Automate IP target registration for RDS behind an NLB, enabling cross-VPC access via PrivateLink, despite RDS not directly supporting NLB registration.
- Discover the IP addresses of the RDS instance endpoints (via DNS).
- Register those IPs as IP targets in the NLB target group.
- Keep the registration up-to-date, especially after a failover or change in IP.
-
- In the same region as your Data Plane
-
Appropriate IAM permissions
- Permissions to manage your VPC Endpoint Service
- Permissions to add allowed principals to your endpoint service
- Typically requires the
ec2:ModifyVpcEndpointServicePermissionspermission
Creating a Private Endpoint
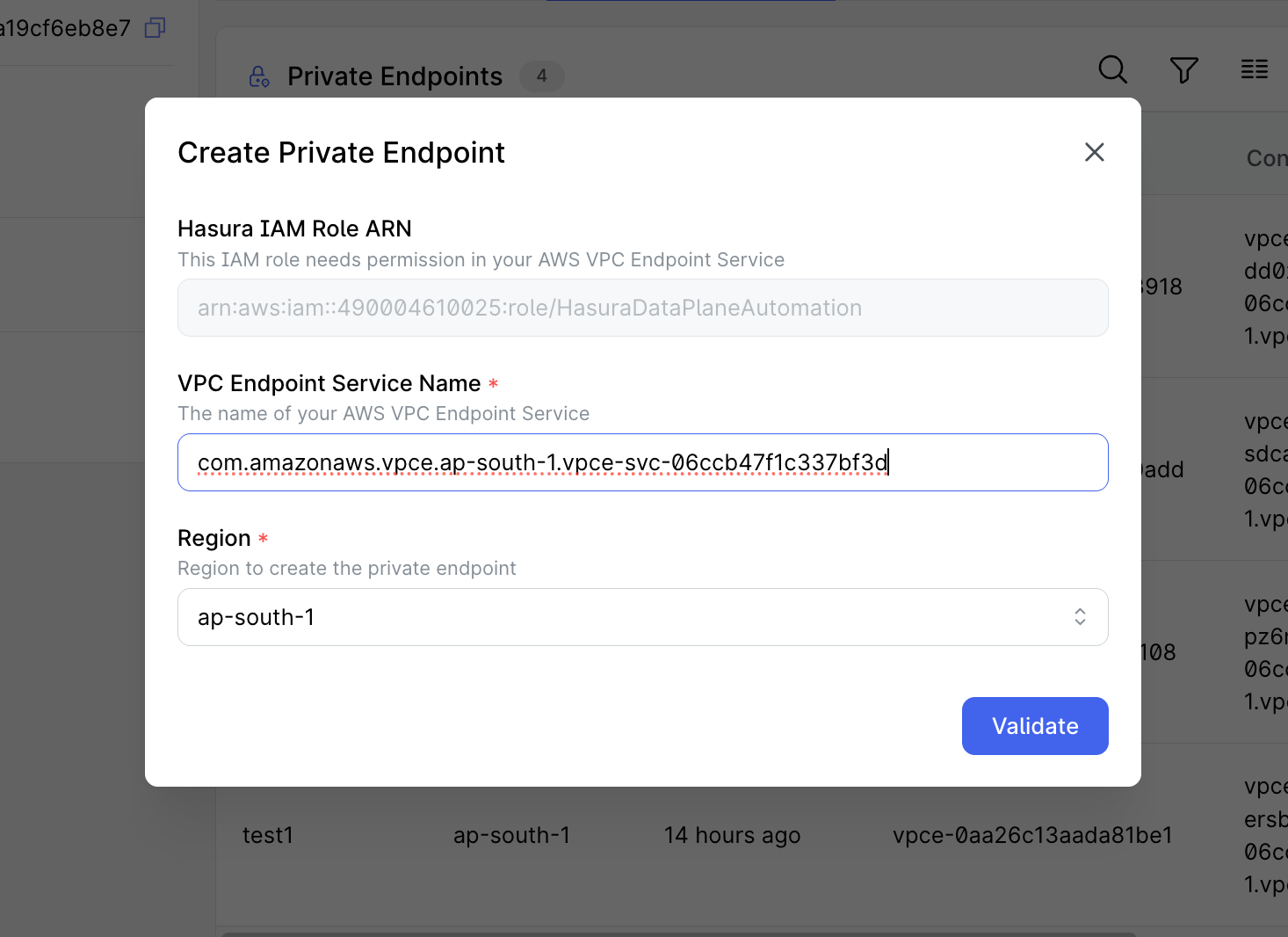
Step 1: Service Principal Information
-
Navigate to your Data Plane details page in the Hasura Console
-
Click the "Create Private Endpoint" button
-
In the modal, you'll see the Hasura IAM Role ARN that needs to be added to your endpoint service permissions
- Format:
arn:aws:iam::DATAPLANE_ACCOUNT_ID:role/ROLE_NAME - This is the AWS IAM role that Hasura's Data Plane will use to connect to your VPC Endpoint Service
- You must add this ARN to the allowed principals in your VPC Endpoint Service settings
- Format:
-
Add this ARN to your VPC Endpoint Service permissions in your AWS account:
- Go to the AWS Console > VPC > Endpoint Services
- Select your endpoint service
- Under "Allowed principals", click "Add allowed principals"
- Paste the Hasura IAM Role ARN and save
-
Enter your VPC Endpoint Service name in the input field
- Format:
com.amazonaws.vpce.REGION.vpce-svc-XXXXXXXX - You can find this in your AWS Console under VPC > Endpoint Services > Service name
- Format:
-
Click "Validate" to proceed
Note: If validation fails, verify that you've correctly added the Hasura IAM Role ARN to your endpoint service's allowed principals list and that you've entered the correct service name.
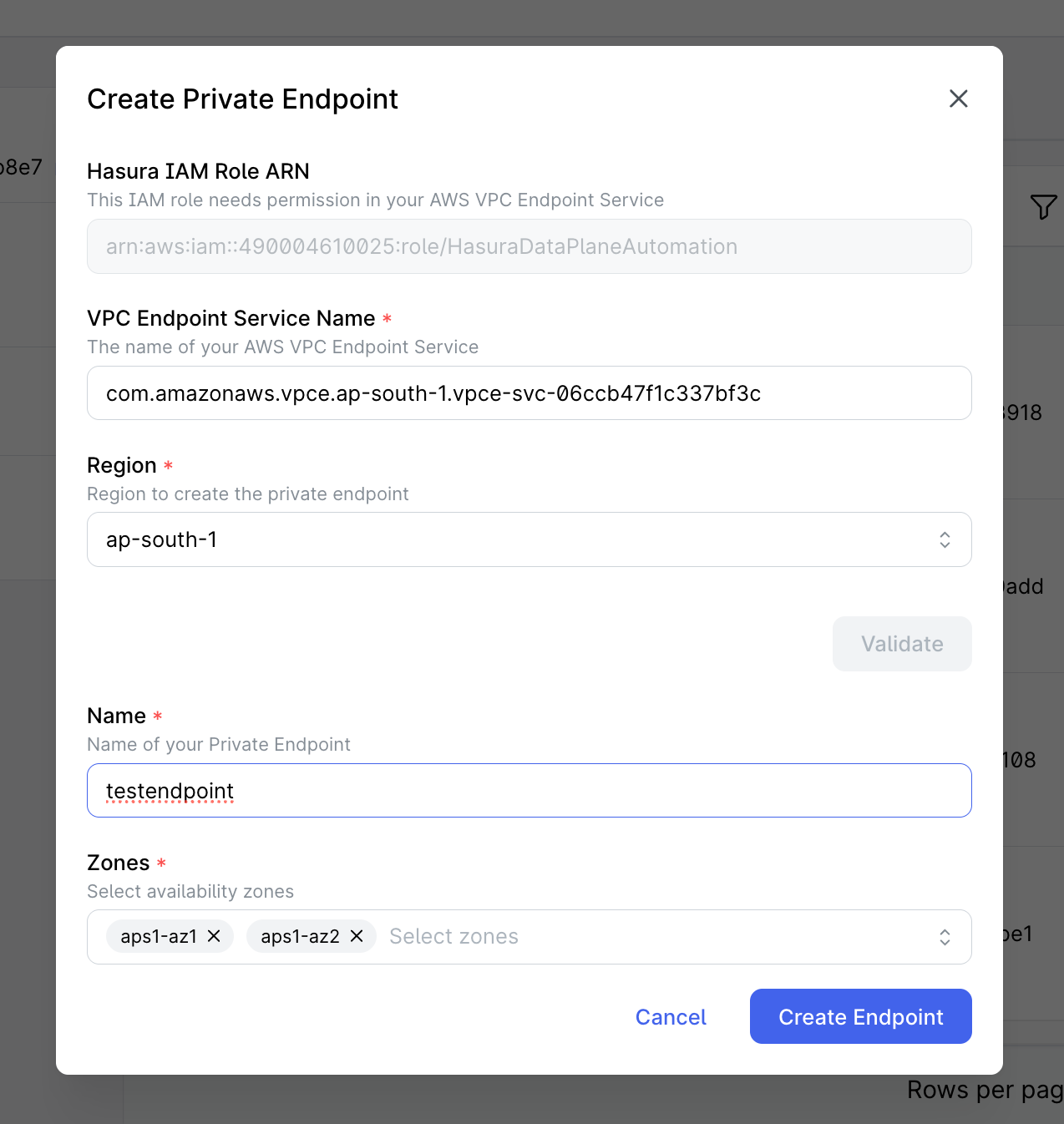
Step 2: Select Availability Zones and Configure Options
-
After successful validation, you'll be prompted to select availability zones
-
Choose the availability zones where you want Hasura to create the endpoint
- It's recommended to select at least two zones for high availability
- Only zones that match with the availability of your VPC Endpoint Service will be available for selection
- Each selected zone will create an Elastic Network Interface (ENI) in the Data Plane VPC
- Select zones that align with where your VPC Endpoint Service is deployed
-
Enter a name for your endpoint
- The name must be unique within your Data Plane
- Name must be between 2 and 20 characters
- Name must start with a lowercase letter
- Name can only contain lowercase letters and numbers
- This name will be used to identify the endpoint in the Hasura Console
Best Practice: Select availability zones where your application workloads run to minimize cross-AZ data transfer costs and latency.
Step 3: Create the Endpoint
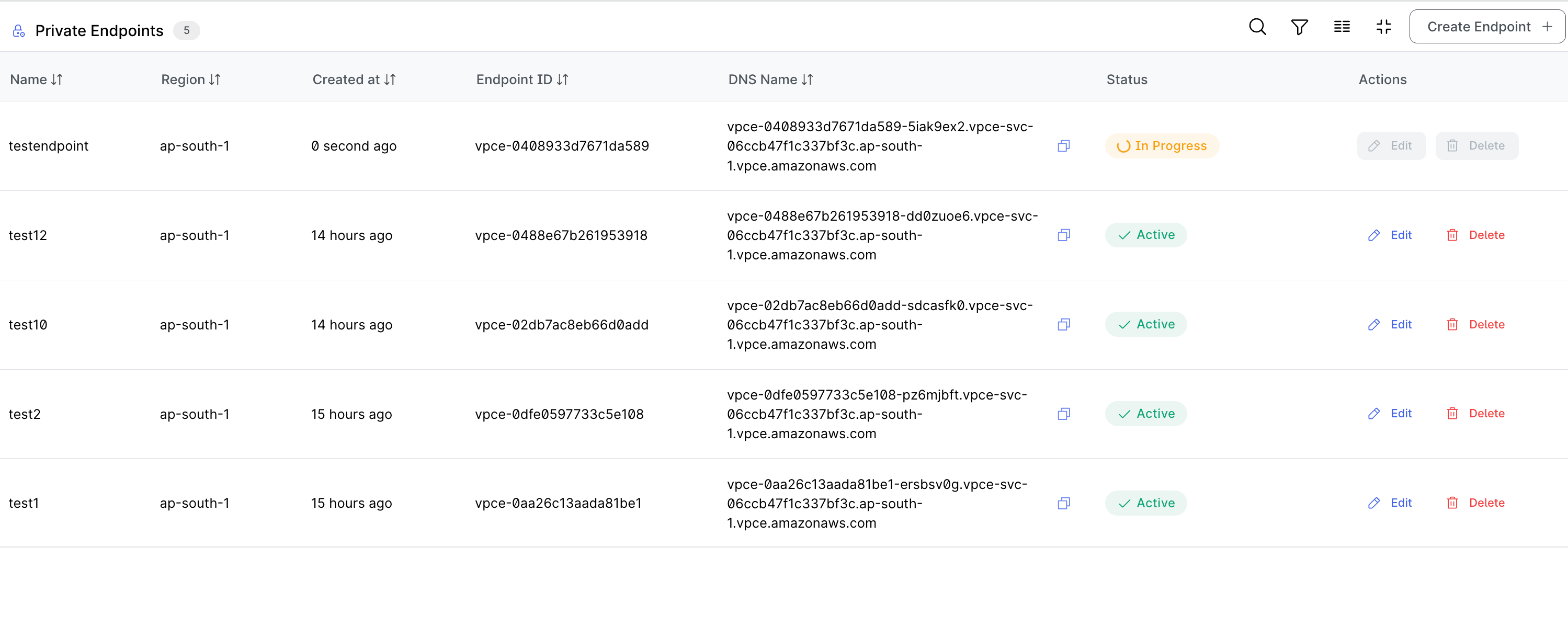
- Review your selections and click "Create"
- The system will initiate the endpoint creation process, which typically takes 5-10 minutes
- You'll be returned to the Data Plane details page where you can monitor the endpoint status
- If you configured your VPC Endpoint Service to require acceptance, the endpoint will initially show a "Pending Acceptance" status
- In this case, you must accept the endpoint connection request in your AWS account:
- Go to the AWS Console > VPC > Endpoint Services
- Find your endpoint service
- Under the "Endpoint connections" tab, find the pending connection
- Select it and click "Accept endpoint connection"
- After acceptance (or immediately if acceptance is not required), the status will change to "In Progress" and then "Active" when ready
Updating a Private Endpoint
You can modify your private endpoint settings after creation to adjust availability zones or enable private DNS. Note that only endpoints in the Active status can be updated.
Step 1: Access the Update Form
- Navigate to your Data Plane details page in the Hasura Console
- Locate the private endpoint you want to edit in the Private Endpoints table
- Click the edit (pencil) icon next to the endpoint
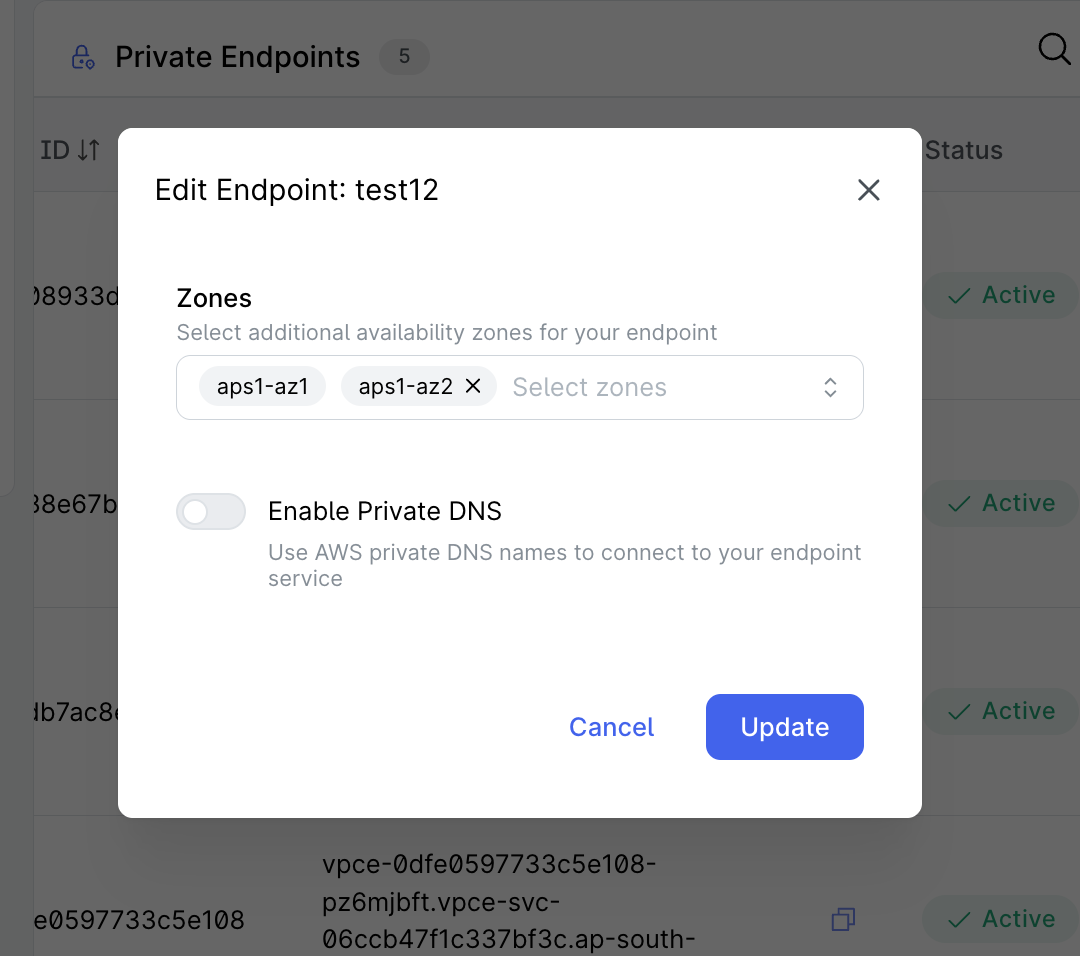
Step 2: Configure Update Options
- In the "Edit Endpoint" modal that appears, you can:
- Select additional availability zones from the dropdown menu
- Only zones that aren't already configured will be available
- You cannot remove existing zones, only add new ones
- Additional zones must be supported by your VPC Endpoint Service
- Toggle the "Enable Private DNS" option to use AWS private DNS names
- This option is only available during edit/update operations, not during initial creation
- Private DNS enablement allows you to use the service's private DNS name instead of the endpoint-specific DNS names
- Note that private DNS can only be enabled for AWS VPC endpoint services that provide a private DNS name
- Select additional availability zones from the dropdown menu
Step 3: Apply the Update
- Review your changes and click "Update" to apply them
- The endpoint will enter the "In Progress" state while changes are being applied
- Changes typically take 5-10 minutes to complete
- You'll be returned to the Data Plane details page where you can monitor the endpoint status
Deleting a Private Endpoint
When you no longer need a private endpoint, you can delete it from your Data Plane. This action cannot be undone and will remove the connection between your VPC and Hasura's Data Plane. Note that only endpoints in the Active, Failed, or Rejected status can be deleted.
Step 1: Initiate Deletion
- Navigate to your Data Plane details page in the Hasura Console
- Locate the private endpoint you want to delete in the Private Endpoints table
- Click the delete (trash) icon next to the endpoint
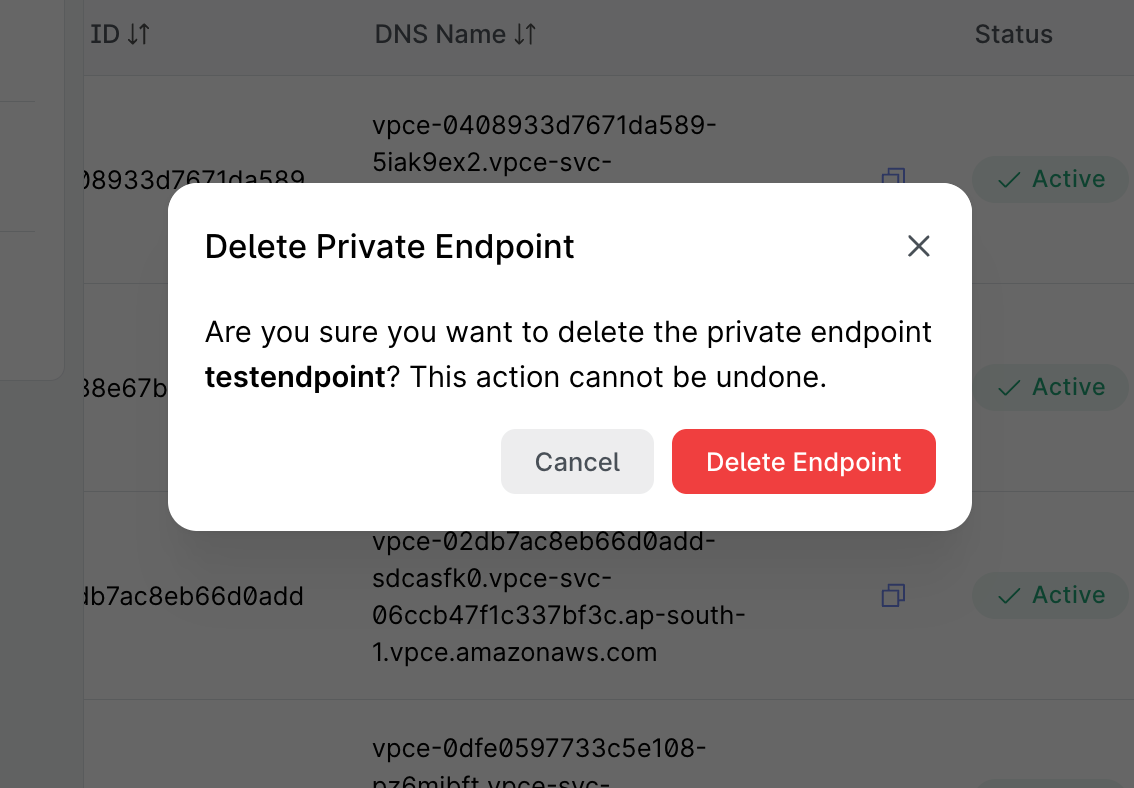
Step 2: Confirm Deletion
- In the confirmation modal that appears, review the endpoint name to confirm it's the correct endpoint
- The modal will display a warning message: "Are you sure you want to delete the private endpoint [endpoint-name]? This action cannot be undone."
- Click "Delete Endpoint" to confirm and proceed with deletion
- Click "Cancel" if you want to abort the deletion process
Step 3: Monitor Deletion Progress
- If confirmed, the endpoint will enter the "Deleting" state while being removed
- The deletion process typically takes 5-10 minutes to complete
- You'll be returned to the Data Plane details page where you can monitor the endpoint status
Endpoint Status Lifecycle
AWS Private Endpoints go through several status states during their lifecycle:
| Status | Description | Action Required | Available Operations |
|---|---|---|---|
| Pending Acceptance | The connection request has been sent to your AWS account and is waiting for acceptance | Accept the endpoint connection in AWS Console | None |
| In Progress | The connection has been accepted and the endpoint is being created or modified | No action needed; wait for completion | None |
| Active | The endpoint is active and ready for use | You can now use the endpoint DNS addresses | Update, Delete |
| Deleting | The endpoint is in the process of being deleted | No action needed; wait for completion | None |
| Failed | The endpoint creation failed | Contact Hasura support for assistance | Delete |
| Rejected | The request was rejected by the service provider | Contact Hasura support for assistance | Delete |
| Expired | The connection request expired | Contact Hasura support for assistance | None |
Using Private Endpoints
Once your endpoint is in the "Active" status, you can use it to establish secure connectivity between Hasura's Data Plane and your data sources. Here's what you need to know:
- The endpoint DNS addresses will be displayed in the private endpoints table
- These DNS addresses represent the connection between Hasura's Data Plane and your VPC Endpoint Service
- For Hasura to connect to your data sources through this private connection, you must configure your data sources in Hasura using the appropriate DNS names
Connecting Your Data Sources
The private endpoint enables secure connectivity between your VPC (where your data sources are) and Hasura's Data Plane. Here's how it works:
- Your data sources (databases, APIs, etc.) in your VPC are accessible through your VPC Endpoint Service
- Hasura's Data Plane connects to your VPC Endpoint Service through the VPC Endpoint
- This ensures that traffic between Hasura's Data Plane and your data sources remains on the private AWS network
- Example architecture:
Hasura Data Plane VPC <---> VPC Endpoint <---> Your VPC Endpoint Service <---> Your VPC with data sources
Important: When configuring your data sources in Hasura, you must use the DNS names provided by your VPC Endpoint Service to ensure traffic flows through the private connection. These DNS names are typically in the format of your service's DNS name or the endpoint-specific DNS names if private DNS is not enabled.
Frequently Asked Questions
Does using private endpoints affect performance?
Private endpoints typically provide more consistent performance compared to public internet connections since they use AWS's private network infrastructure and avoid internet congestion.
Can I use the same private endpoint for multiple applications?
Yes, a single private endpoint can be used by multiple applications within the same VPC or connected VPCs (via VPC peering or Transit Gateway).
How are private endpoints billed?
AWS charges for VPC endpoints based on hourly usage and data processing. Refer to the AWS PrivateLink pricing page for current rates.
Can I connect to my VPC Endpoint Service from outside AWS?
No, VPC Endpoint Services are only accessible from within AWS. To access from outside AWS, you would need to set up a VPN or Direct Connect to your AWS VPC.
Troubleshooting
Common Issues
| Issue | Possible Causes | Resolution |
|---|---|---|
| Endpoint stuck in "Pending Acceptance" status | - Connection request not accepted - AWS Console permissions issue - Endpoint Service requires acceptance | - Accept the endpoint connection in AWS Console under VPC > Endpoint Services - Verify you have permissions to accept connections |
| Validation errors | - Incorrect Hasura IAM Role ARN - ARN not added to allowed principals - Incorrect service name | - Verify the ARN is correctly added to your endpoint service permissions - Check for typos in the service name |
| Cannot connect to endpoint | - Security group restrictions - Route table configuration - DNS resolution issues | - If your database is behind a load balancer, ensure that the Enforce inbound rules on PrivateLink traffic option (found under the Load Balancer’s Security tab) is disabled. If your setup requires this option to remain enabled, make sure that your security group explicitly allows inbound access from Hasura's VPC CIDR over the appropriate database port (e.g., PostgreSQL port 5432). For further troubleshooting, contact Hasura support for assistance |
| Failed to create endpoint | - Service quota limits - Network configuration issues | - Contact Hasura support for assistance |
Before Contacting Support
-
Verify VPC Endpoint Service Status:
- Check the status of your VPC Endpoint Service in AWS Console > VPC > Endpoint Services
- Ensure it's available and properly configured with your Network Load Balancer
-
Verify Allowed Principals:
- Confirm that the Hasura IAM Role ARN has been added to the allowed principals list
- Check for any typos or formatting issues in the ARN
-
Check Service Name:
- Verify that you've provided the correct VPC Endpoint Service name to Hasura
- The format should be
com.amazonaws.vpce.REGION.vpce-svc-XXXXXXXX
Getting Help
If you encounter issues with private endpoints, especially if you see Failed, Rejected, or Expired statuses, or if you cannot connect to an endpoint, contact Hasura support through your enterprise support channel. These issues often require investigation on Hasura's side to resolve.
