An “Authentication Service Provider” refers to an entity that provides authentication services. The Authentication Provider abstracts the complexity of implementing the authentication system manually from scratch so you can focus on more important tasks.
This article presents the benefits and drawbacks of using an Authentication Provider and compares the existing ones that support JWT integration.
Pros and Cons of Auth Providers
Before choosing an Auth Service Provider, it’s essential to assess the benefits and drawbacks of using one.
Pro: Abstracts Complexity
Using an Authentication Service Provider abstracts the complexity of implementing the auth system yourself. Building such a system is a complex, lengthy process requiring many resources.
You can use an existing solution that frees up those resources for other, more critical tasks.
Pro: No User Information Storage
Storing confidential information about people is not something to take lightly. Opting to use a provider means you do not have to worry about storing the users’ details on your servers.
Pro: Leverage Social Logins
You can enable social logins with minimal effort when using an Auth Service Provider. Social login refers to logging in using an existing social network account such as Twitter, GitHub, Google, and so on.
Implementing each social provider individually requires effort and resources. When using an Auth Provider, adding social logins becomes easier and quicker.
Pro: Better Security
Opting to use an Auth Provider means better security. The whole focus of an Auth Provider is on authentication and authorization. That means they are better trained and equipped to keep the users’ information secure.
Cons: Difficult to Migrate
Once you choose an Authentication Service Provider, it can be difficult to migrate away. Changing to another provider or rolling a proprietary system can be difficult.
It’s essential to decide whether it makes sense to use an Auth Provider or not. If you choose to do it, make sure you choose the provider that fits your needs and requirements.
Cons: Provider Lock-in
Another drawback is that you might become too reliant on the provider you are using. The reasons might be that your implementation is too specific to that vendor, or it’s nearly impossible to export your current user data.
Migrating to another provider might become too costly and time-consuming, so you are locked with the current one.
Cons: Costs
In the beginning, the costs might not be an issue. However, after the application grows bigger and has more users, the costs can become a problem.
Many of the Auth Providers charge based on the number of monthly active users. The more users you have, the bigger the bill becomes.
Conclusion
Should you use an Authentication Service Provider or implement a proprietary system? There is no definitive answer.
The decision to use a Provider or not depends on many factors. For some, using an Auth Provider is the appropriate solution, whereas, for others, it is not.
In case you decide to use one, keep reading to learn about the various Authentication Service Providers available.
Choosing an Auth Provider
The article compares the following Authentication Service Providers:
- Auth0
- Firebase Auth
- Clerk
- KeyCloak
- Cognito
- SuperTokens
- Nhost
These auth providers are evaluated based on six evaluation criteria.
1. Open Source
An open source project comes with a handful of benefits. One benefit would be the cost savings. Since they are open source, they do not require licensing or usage fees.
Another benefit is flexibility. If the business requirements change or you need additional features, you can modify and extend the code yourself. You do not have to ask the vendor for changes or to change it altogether.
It’s important to mention transparency as well. The code is available for everyone to see. Since so many professionals have access to the code, they can make the software better and more secure.
There are other benefits of using an open source auth provider as well, but these benefits drive the point home.
2. Custom JWT Claims
When integrating any Authentication Service Provider with Hasura, it’s important to ensure they support custom JWT claims.
Hasura checks the custom JWT claims to learn about the role of the user making the request. As a result, Hasura can apply the appropriate authorization rules.
{
'x-hasura-default-role': 'user',
'x-hasura-allowed-roles': ['user'],
'x-hasura-user-id': user.user_id
};
The above snippet shows an example of custom JWT claims. It contains essential information about the request.
3. Single Sign-On (SSO) Support
In the simplest terms, SSO refers to the type of authentication where the user logins to multiple platforms with one set of credentials.
One example is the Social SSO, where the user uses a social network account such as the Google account to log into an application.
4. Machine to Machine Authentication
It’s not always the users who make the requests. There are scenarios where two machines communicate between them. There is no user to input the credentials, so the client (another machine) needs to be authenticated in another way.
Machine to machine (M2M) authentication refers to authenticating machines without user input. That’s possible by using the OAuth 2.0 Client Credentials Flow. The credentials include a client_id and client_secret, which are used to authenticate the client.
5. Free Tiers
All the auth providers from this article have a free tier. The difference lies in what they offer in that tier.
They measure the monthly active users (MAUs) and charge based on that. As a result, some providers offer a free tier with thousands of MAUs, whereas some offer only a couple hundred MAUs.
6. Ease of Integration
The integration of an auth service provider depends on many factors. It’s challenging to present how easy or difficult it is to integrate a provider.
However, there are some points that might indicate the difficulty level of the implementation, such as:
- the quality of documentation
- available SDKs
- the amount of configuration required
- the available material
Provider Comparison
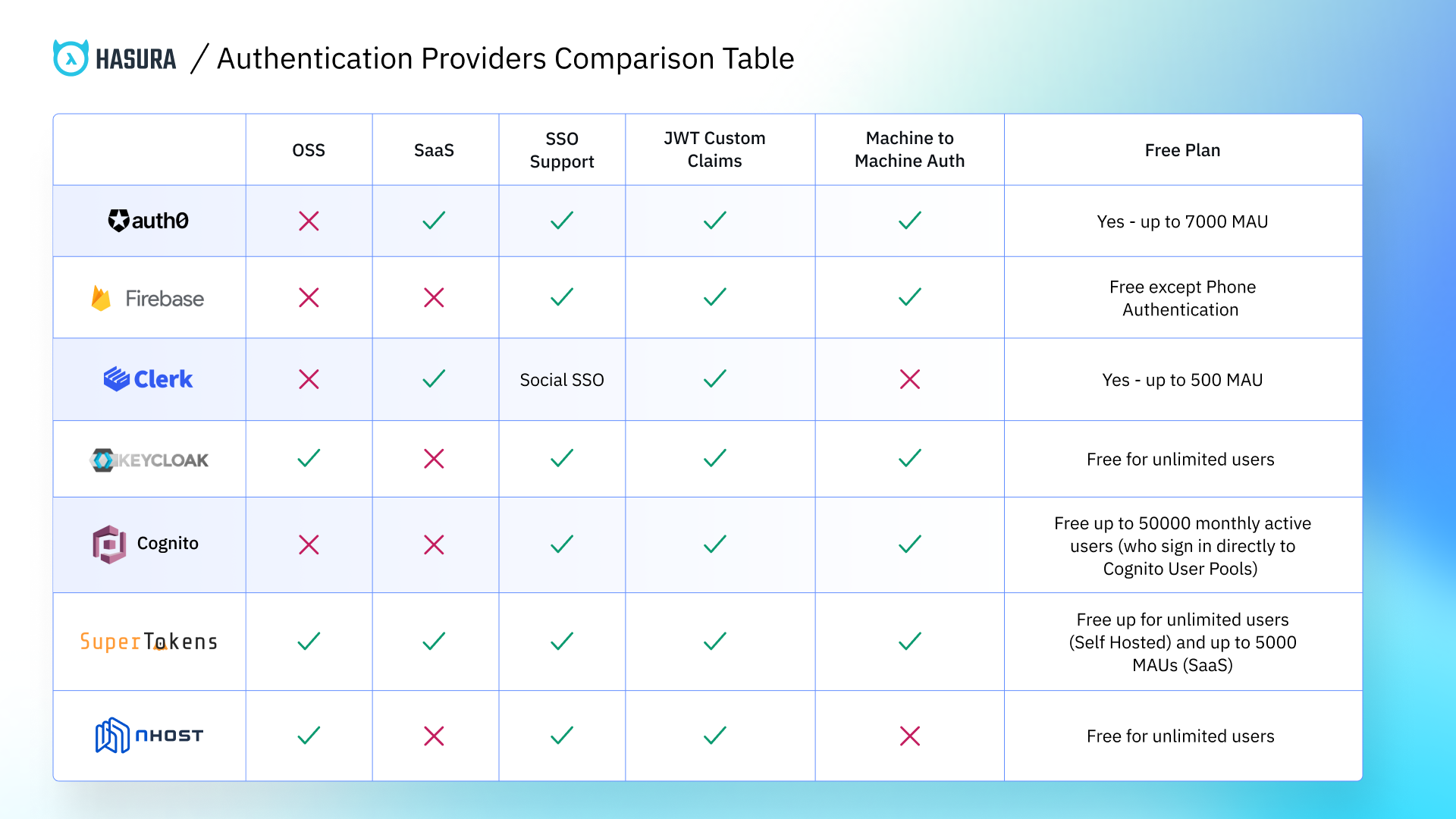
The image illustrates a comparison between the Auth Providers presented in this article.
Auth0
Auth0 is a well-established and popular solution for auth services. It comes with a generous free tier and has support for most of the things you need.
| Open Source |
No |
| SaaS |
Yes |
| SSO Support |
Yes |
| JWT Custom Claims |
Yes |
| Machine to Machine Authentication |
Yes |
| Free Plan |
Yes - up to 7000 MAU |
When it comes to the ease of integration, Auth0 is neither easy nor difficult to integrate. Since it’s a well-established and widespread solution, a great deal of material is available to help you with the integration. The amount of configuration you need to do depends on the type and complexity of your application.
Learn how to integrate Auth0 with Hasura
Firebase Authentication
Firebase Authentication is another popular auth service that allows you to add authentication to your applications.
Firebase allows you to add sign-in methods such as:
- identity providers such as Google, Facebook, and others
- email and password
- phone
| Open Source |
No |
| SaaS |
No |
| SSO Support |
Yes |
| JWT Custom Claims |
Yes |
| Machine to Machine Authentication |
Yes |
| Free Plan |
Free except for Phone Authentication |
The amount of available resources makes the integration process more straightforward. The Firebase community creates lots of open source resources you can use. It’s also a well-established provider, which means that you are likely to find a solution to almost any problem.
Lastly, it has in-depth documentation covering how to implement Firebase Auth in both web and mobile applications.
Learn how to integrate Firebase with Hasura
Clerk
Compared to the other providers, Clerk is the newest one. Clerk enables you to implement sign-up, sign-in, and user profiles into your applications. According to their website, they are a “complete Customer Identity Platform".
Clerk also comes with Hasura support. They have a special documentation section that showcases how to integrate Clerk with Hasura.
| Open Source |
No |
| SaaS |
Yes |
| SSO Support |
Social SSO |
| JWT Custom Claims |
Yes |
| Machine to Machine Authentication |
No |
| Free Plan |
Yes - up to 500 MAU |
Since it’s relatively new, you might run into issues that are not documented/solved yet. Other than that, Clerk has extensive, in-depth documentation.
The configuration needed to integrate Clerk with your application is minimal. You need a Clerk account, and then you can use the SDKs and components provided by them.
Learn how to integrate Clerk with Hasura
Keycloak
Keycloak is a popular open source Auth Service Provider. Since it’s open source, you can self-host it, which means it’s free regardless of the number of monthly active users.
Even though it’s open source and open to everyone to contribute, the project is maintained by Red Hat. That means you can trust the project.
Keycloak supports most authentication use cases, and it’s also free, so it can be a great choice.
| Open Source |
Yes |
| SaaS |
No |
| SSO Support |
Yes |
| JWT Custom Claims |
Yes |
| Machine to Machine Authentication |
Yes |
| Free Plan |
Free for unlimited users |
Keycloak has a moderate level of implementation difficulty. Besides integrating Keycloak into your applications, you also have to take care of deployment and maintenance.
Even though it might look complicated at first sight, you can get accustomed to Keycloak quickly. It also is an established product, which means you are likely to find solutions to most of your issues. Lastly, it has good documentation.
Learn how to integrate Keycloak with Hasura
Cognito
Cognito is Amazon’s product for handling authentication. It allows you to implement authentication into your web and mobile applications.
Cognito is one of the most generous auth providers, giving you a free plan with up to 50,000 monthly active users. If costs are a concern and you want a managed solution, Cognito is an excellent choice.
| Open Source |
No |
| SaaS |
No |
| SSO Support |
Yes |
| JWT Custom Claims |
Yes |
| Machine to Machine Authentication |
Yes |
| Free Plan |
Free up to 50000 monthly active users (who sign in directly to Cognito User Pools) |
Regarding the ease of integration, Amazon Cognito can get quite challenging to implement compared to other providers. Cognito requires a complex setup, even for basic applications.
However, there are many official and community materials to help you integrate Cognito with your application. A handful of SDKs and sample apps are also available to help and inspire you.
Learn how to integrate Cognito with Hasura
SuperTokens
SuperTokens is a relatively new service. It comes with support for almost everything you need, and it’s also open source. That means you can self-host it and avoid extra charges. If you choose to self-host, it’s free forever for unlimited users.
SuperTokens comes with Hasura support, having a special section on how to integrate SuperTokens with Hasura.
| Open Source |
Yes |
| SaaS |
Yes |
| SSO Support |
Yes |
| JWT Custom Claims |
Yes |
| Machine to Machine Authentication |
Yes |
| Free Plan |
Free up for unlimited users (Self Hosted) and up to 5000 MAUs (SaaS) |
When it comes to the ease of integration, you might encounter some difficulties when trying to integrate it with your application. The reason is that it’s a new service and there is not a lot of material available on the internet at the moment.
Regarding configuration, it’s reasonably easy to get started with SuperTokens since the documentation provides all the settings and information you need.
SuperTokens also has guides on integrating SuperTokens with Hasura and sample SuperTokens + Hasura demo applications.
Learn how to integrate SuperTokens with Hasura
Nhost Authentication
Nhost Authentication is an open source authentication service for Hasura. With Nhost Authentication, people can sign-in with:
- Email and password
- OAuth Providers such as GitHub, Google, Apple, Facebook, Twitter, LinkedIn and others
- Magic links
- SMS
Since it's an open source project, you can self-host it and avoid the extra charges you would pay when using a managed service.
| Open Source |
Yes |
| SaaS |
No |
| SSO Support |
Yes |
| JWT Custom Claims |
Yes |
| Machine to Machine Authentication |
No |
| Free Plan |
Free for unlimited users |
When it comes to the ease of integration, Nhost Authentication is fairly straightforward to integrate with Hasura applications. You can either create an application through Nhost, which gives you an out-of-the box backend with Hasura, Hasura Auth and Postgres or you can use the Nhost Authentication Docker image to self host it.
You can check Nhost Authentication here.
A Note on Scalability
Scalability refers to the authentication service’s ability to handle your application growth and changes in business requirements. The auth service should keep up with your user growth and requirements change without affecting your application.
If you decide to use a self-hosted solution, you have full responsibility when it comes to scaling. You need to manage the database, servers, and the whole infrastructure. It’s your responsibility to make sure everything works smoothly.
When you use a managed solution, the auth provider takes care of scaling up and down. The auth provider has pre-defined rate limits and quotas, which they use for scaling.
Conclusion
All providers presented in this article are excellent choices, but there is no one universal answer. Choosing an Authentication Service Provider depends on one’s needs and requirements.
SuperTokens and Clerk are two notable providers that support Hasura officially. “Support" means that they have a special section in their documentation illustrating how to integrate them with Hasura. That’s a plus, and it helps a lot when integrating any of them with Hasura.
It’s important to note that this is not an exhaustive list. There are other providers available which are not present in the article. However, the article will be updated occasionally, and new providers will be added.